Plug-ins and browser add-ons should not be confused. An add-on is a browser extension that you can usually download from a place like the Chrome store. Add-ons are run in the browser process. Examples of browser add-ons are AdBlock and Chostery.
In contrast, plug-ins are usually pre-installed in the browser or downloaded from a third-party website. Examples of plugins are Flash and Widevine. The plug-in usually runs in a separate process, which has all the rights of the currently active user, which may lead to various vulnerabilities.
1. The risk of enabling the plugin
Some plug-ins such as Flash or Widevine have a documented API that allows them to obtain various uniquely identifiable data points from the host computer. Other plugins may also have such an API, whether it is public or private, it may threaten online privacy. Since plug-ins are essentially closed-source binary files, there is no reliable way to evaluate which security vulnerabilities a plug-in may have.
2. Generate fingerprints through the enumeration method
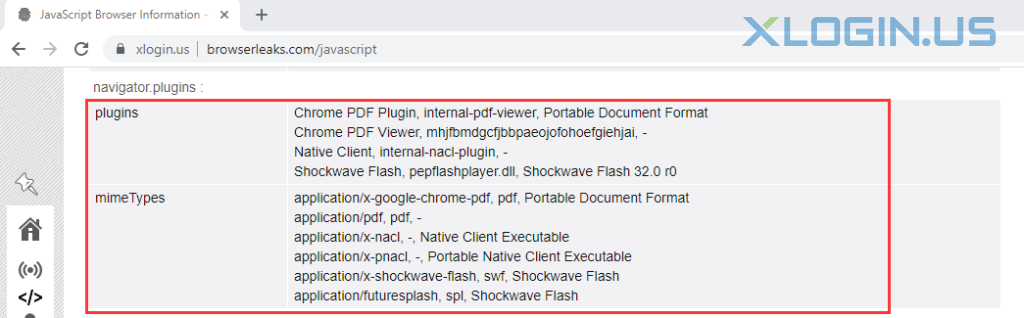
Another risk comes from the browser plug-in enumeration. Even if a website is unable or unwilling to obtain uniquely identifiable data through the plug-in API, it can still collect uniquely identifiable data as a list of plug-ins. A list of plug-ins with each version can significantly reduce the segments to which users belong. Multiple browsing sessions can be linked together individually based on this data, or combined with other data points.
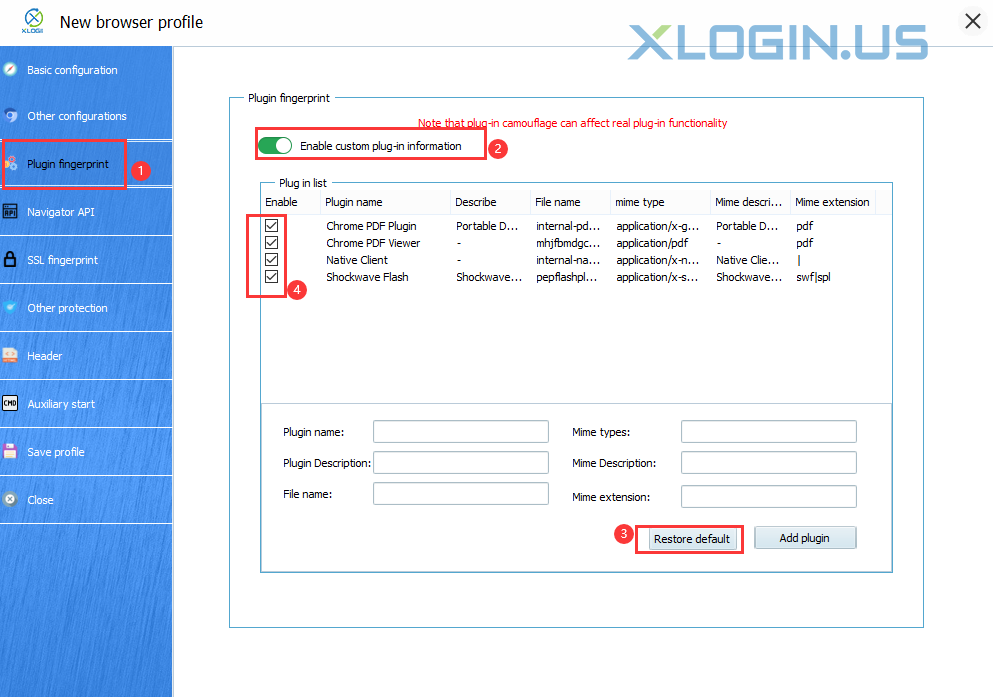
3. Default plug-ins in Firefox and Chrome
By default, Firefox has no plug-ins installed. Chrome has four bundled plug-ins:
(1) Chrome PDF
(2) Chrome PDF viewer
(3) Native client
(4) Widevine Content Decryption Module
For XLogin browser custom plugin setting details, please refer to "Custom Plugins Tutorial".